Security Tips and Features: Identifying Spam-Tech Tip for July 9, 2024
In this week’s Tech Tip, we discuss best practices when identifying spam email messages and senders. We’ve all been there. It’s been a hectic day, and you receive a rushed message to do something important. Stop! Wait.
Review the sender and the message. Is it someone you know, and is the email address correct? Does it seem out of character to receive a demanding message from the sender? By remaining cautious and knowing the common signs of a spam, spoof, or phishing message, you can protect your computer and personal information from potential harm. Let’s dive in!
Spot the Difference in Spam Messages
Let’s explore the differences in types of ‘social engineering’ messages:
Spam refers to unsolicited or unwanted emails that are sent to many recipients. Usually, this is an email that will feel intrusive, unwanted, and may have ‘advertising’ or ‘services offered’ elements to them.
Phishing is an attempt to trick individuals into revealing their sensitive information—this could be your login credentials, identity, or financial-related information. Often the sender will pose as a trustworthy entity (your boss, a bank, the government, a well-known company) and include links in messages that appear to be from legitimate sources. These types of emails are designed to steal information.
Spoofing is when attackers impersonate someone to gain access to sensitive information. For an email spoof, the message may appear to be from a trusted source, such as a fake IP address that impersonates a trusted device on a network, or the message or text could appear as an attempt to intercept communication between two parties to manipulate the outcome of something (Man-in-the-Middle attack).
Smishing (SMS or Short Message Service Phishing) uses text messages to try to steal or reveal sensitive information like phishing and may also contain links to fake websites from sources that look legitimate, prompting individuals to do something for the sender: whether it is giving away confidential information or asking individuals to download malware, or purchase items.
How to Identify Spam & Phishing Emails
Check the Sender and Address
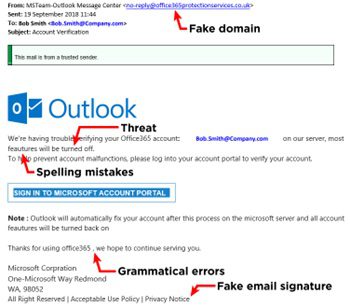
- Check the sender’s name and email address. If they do not match, or if the email address is unfamiliar, generic, or contains random letters or numbers, it is likely spam.
- Check the reply-to address in the message. If it is different from the sender’s address, or if it is a no-reply address, it is likely spam.
- Check the domain name of the sender and the links in the message. If they are unfamiliar, misspelled, or contain random letters or numbers, it is likely spam.
- Does the sender’s address pretend to be a familiar (known) address but not match the message content or the tone of the (known) sender? It is likely phishing.
- If you are unsure: call or ask (known) senders by phone or in person to verify the email or text message was sent by them. If it was not, it is likely phishing.
Review the Subject Line and Message Body
- Check the subject line and the message body. If they are vague, irrelevant, misleading, or contain spelling or grammatical errors, it is likely spam.
- Check the tone and style of the message. If it is too urgent, too good to be true, too friendly, or too impersonal, it is likely spam.
- Be wary of urgent or threatening language, or messages requesting personal or financial information, or senders asking you to purchase something ‘in a hurry.’ This is likely phishing.
- Hover over links to check their destination before clicking. If the website link looks suspicious, it is likely phishing.
- Check the links and attachments in the message. If they are suspicious, unknown, or irrelevant, do not click on them or download them. They may contain malware or lead you to phishing websites.
- Check the unsubscribe option in the message. If it is missing, hidden, or does not work, it is likely spam.
- Check the message for requests or demands for personal or financial information, such as passwords, bank accounts, credit cards, or social security numbers. If it asks you to provide or verify such information, it is likely phishing or spam.
- Check the header and footer of the email message—do logos look askew, are the colors a bit different, or does the signature seem incorrect? It is likely phishing or spam.
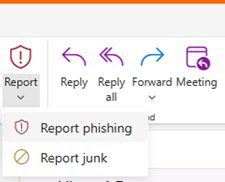

(Above: Report and Block Settings within New and Classic Outlook)
What to Do After Receiving Spam or Phishing Emails
Now that you’ve verified and identified your email message as phishing, a spoof, or spam, take the next steps:
- Block the Sender.
- In classic Outlook: from the Home tab, select ‘Block Sender.’
- Report the Sender email as ‘Phishing’ or ‘Junk.’
- In new Outlook: from the Home tab, select ‘Report Phishing’ or ‘Report Junk.’
- Report the email message to your IT provider if appropriate.
- Fill out email message abuse forms with your email provider if appropriate.
For larger scale phishing or smishing campaign-style cyber-attacks, report them to the FCC:
Reporting phishing, smishing, and more, to the FCC.gov Hotline
Be sure to follow along with us in our Tech Tip series for more technology tips.
Reach Out to TechWise Group
Interested in learning more about Security and next steps for your business? Reach out to TechWise Group. We’ll help you make the most of your Microsoft tools.
Important Microsoft Announcements:
- Maximize your organization’s Security with Secure Score and MFA:
- Get to know your Secure Score—your essential tool for proactive threat management.
- Enabling Multi-Factor Authentication (MFA) is the best way to prevent cyberthreats.
- Give your business a productivity boost with Microsoft Copilot:
- Get started with Copilot consulting services to organize and secure your data, while also training you and your team.
- Keep your infrastructure up to date:
- Windows 10 reaches End of Support (EOS) on October 14, 2025.
- Windows 11 feature update 24H2 is now broadly available (January 2025).
- Windows 11 version 22H2 Home and Pro editions will reach end of service (October 8, 2024) and will be required to upgrade to version 23H2 to continue receiving security updates.
- Windows 11 Enterprise and Education editions with 22H2 will continue to be supported after October 8, 2024.
- Contact TechWise Group to get started or to put a plan in place.