
Gone Phishing – Tech Tip for November 19, 2019
Let’s say you received an email from a reputable company you know well. Heck, maybe it’s from your own company. The email is reminding you that one of your many corporate passwords has expired and you need to renew it within 24 hours—or else.
This is how you become victim to a phishing attack. And there are telltale signs for discerning whether an email you received is corrupt.
Since phishing is one of the easiest ways to get scammed, we are continuing our cybersecurity theme with help from security experts Sean Lawson and Dan Causland. This week, they’re showing us how to detect an attack before you find yourself at the end of someone’s hook…
What is phishing?
Phishing is a form of social engineering. It’s when a hacker pretends to be someone they’re not on email or text in order to nab your personal or corporate information (like your login credentials or credit card).
Email is usually the most common form of phishing bait. Once a fraudulent message is cast, it’s designed to trick you into sharing personal information or clicking on a link that will automatically install malware on your device. If you get duped, the hacker can defraud, steal, or gain access to your information, assets, or accounts.
How can you prevent a phishing attack?
Familiarize yourself with different types of phishing tactics:
Spear Phishing: This is a more personal attack. Spear phishing always targets a specific person or organization. The perpetrator has done their research and gathered some knowledge of who you are and will use that information to trick you.
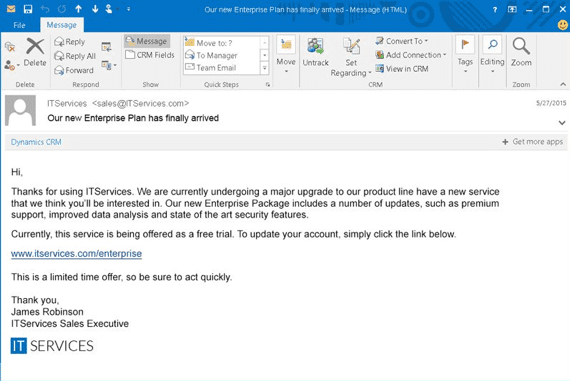
Spoofing: A scam where an email sender is pretending to be somebody else. The perpetrator is skilled at making an email from a trusted company look legit by including brand details like logos.

Look for red flags:
- Check the sender email address. Scammers will use email addresses that may look similar to the real thing, but they will have slight differences (maybe they use a different domain name like .com instead of .org or replace the letter “l” with a capitalized “i” or number “1”).
- If there is a link in the email, you can check if it’s fraudulent by hovering your cursor over it (don’t click!). You will see the actual web address in the bottom left-hand corner of your window.
- Look for poor grammar, misspellings, or unprofessional wording in the message.
- Be wary of emails with unwarranted urgency or solicitation. For example, emails that demand money or say you have less than 24 hours to do something.
Follow best practices:
- Don’t put personal information online and don’t casually give out any usernames or passwords over email.
- Create complex passwords and avoid reusing old passwords.
- Don’t click links in emails. Go directly to the known company site on your web browser.
- Update your software regularly.
- Do not open any email attachments you are not expecting.
- Understand that using antivirus software to scan an email message or file doesn’t automatically protect you from phishing. Phishing is all about using social tactics to trick you.
If you know an email is a phishing attempt, delete it immediately. But if you are ever unsure, forward it to support@techwisegroup.com and we will validate it for you. For more information about phishing, check out Microsoft’s comprehensive article.
Also, if you are interested in securing your Office 365 services to better protect your company from threats like phishing attacks, please reach out to TechWise Group. We can help reduce your exposure to scammers by enabling some of the best defense mechanisms like Multi-Factor Authentication.
